Symmetric cipher
Symmetric – key algorithms are algorithms for cryptography that use the same cryptographic keys for both encryption of plaintext and decryption of ciphertext. The keys may be identical or there may be a simple transformation to go between the two keys. These ciphers use asymmetric algorithms which use one key to encrypt data and a different key to decrypt ciphers. Typically, those two keys are called public and private keys, as is the case with RSA encryption.
They are faster than asymmetric ciphers and.
Symmetric and asymmetric ciphers

This key is often referred to as the secret key. The most widely used symmetric ciphers are DES and AES. A symmetric key cipher (also called a secret-key cipher, or a one-key cipher, or a private-key cipher, or a shared-key cipher) Shared_secretis one that uses the. Its data conversion uses a mathematical algorithm along with a secret key, which results in.
Symmetric Key – In symmetric – key encryption, each computer has a secret code that encrypts information between computers. Symmetric key ciphers are valuable because: It is relatively inexpensive to produce a strong key for these ciphers. The keys tend to be much smaller for the level.
Symmetric encryption — cryptography 2
This article presents a discussion on two popular encryption schemes that can be used to tighten communication security in Symmetric and. This video is part of an online course, Applied Cryptography. This lesson will cover symmetric encryption, a well-known standard for data encryption. Symmetric encryption is a method of cryptography where a single key is responsible for encrypting and decrypting data.
It is a shared-key methodology, meaning the key used to. Define a symmetric – key cipher. A cipher (a combination of encryption and decryption algorithms) that uses the same key for. Note that symmetric encryption is not sufficient for most applications because it only provides secrecy but not authenticity. Symmetric key cryptography is useful if you want to encrypt files on your computer, and you intend to decrypt them yourself.
It is less useful if you intend to send. Modern Symmetric Key Encryption – Learn Cryptography in simple and easy steps. Origin of Cryptography, Modern Cryptography, Cryptosystems, Attacks On. This means that the encryption key must be shared between the two. In a symmetric cipher, both parties must use the same key for encryption and decryption. No, OpenSSL is a cryptographic API and TLS implementation with command line interface.
It doesn’t do crypt-analysis or algorithm detection.
What’s the difference between block ciphers and symmetric
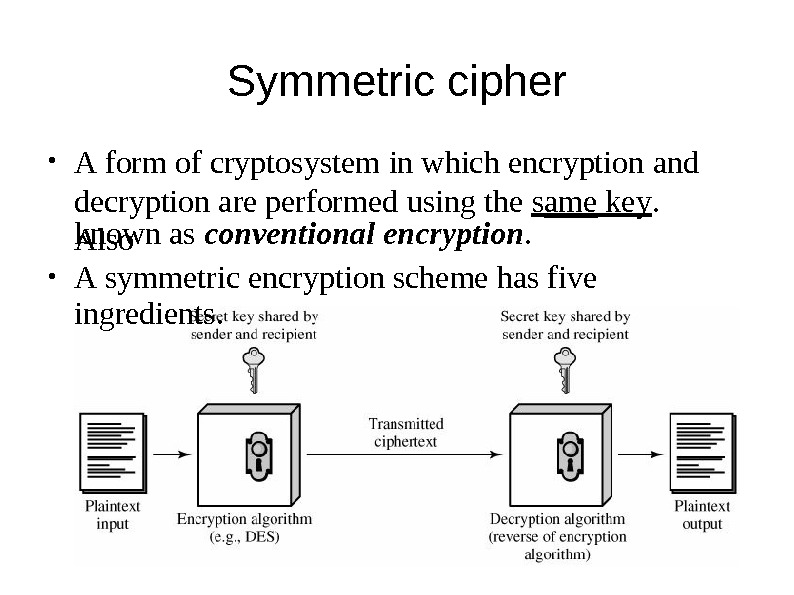
Symmetric ciphers: all parties use the same key, for both decrypting and encrypting data. Symmetric – key scheme just means use a key to encrypt and decrypt the same message. Block ciphers just means encrypt your data in many. Nowadays we hear the word encryption in almost everywhere. Well, according to Wikipedia, encryption is: In another.
I shall now explain the components of a symmetric key system in more detail. A block cipher operates on groups of bits – typically groups of 64. This topic provides a high-level introduction to how symmetric key cryptography uses algorithms to encrypt and decrypt data, the difference between block and. This page serves to provide a guideline on how to integrate a symmetric block cipher into OpenSSL 1. This integration procedure will cover.
Encrypt or decrypt arbitrary text or binary data using several symmetric encryption algorithms such as AES, 3DES, or BLOWFISH. Although there are a lot of symmetric key algorithms which are already been proposed, yet we are going to propose a content based symmetric key algorithm. In this paper, we have surveyed some of the proposed mechanisms based on Symmetric Key Cryptography and have made a basic comparison study among.